There exists a very significant gap in cybersecurity solutions for civil society in the Global South, particularly in Africa. This is largely due to the very low ratio of cyber security practitioners to civil society organisations in the region. This shortage has critically impacted the outcomes, scale and sustainability of many cybersecurity interventions, most of which are designed to be one-offs to accommodate the thousands of organisations who still cannot access critical cybersecurity services. But this- one-off approach- is both unsustainable and ineffective on the long term, as organisations at-risk require all-year round protection against state-sponsored threat actors, not just one-time support.
This challenge was the starting point of our ideation at Resilience Technologies. In this 2023 project, we sought to find the most cost-effective and contextually relevant model of cybersecurity intervention for civil society by collecting and analysing data from a sample size population of at-risk civil society, activists and media organisations in sub-Saharan Africa.
From the result and data of that project, we had two key questions:
- What is a high-impact cybersecurity challenge that remains unsolved for civil society?
- How might we solve this challenge?
Our exploration of the first question presented us with a handful of challenges, with one emerging as the most critical and strategic: Threat Management.
We discovered that the three pillars of threat management – Prevention, Detection and Response – are rarely integrated within a single solution or intervention in the internet freedom space. Among these, Incident Response is the most widely deployed but often stands alone without other complementary preventive and detective measures. Further research revealed that the current incident response approach -which is similar for most help desks and civil society across the Global South- leaves many gaps for threat actors to exploit.
Incident Response Approach
Typically, when an at-risk organisation or individual suspects or experiences an attack on their infrastructure, they report it to a help desk or security operator. A help desk staff or an external service provider is then assigned to the case after which they arrange for a meeting to gather details about the attack, and then provide support for containment and recovery.
This approach has significant limitations in effectively addressing the diverse and sophisticated risks and threats that civil society face, particularly in the Global South.
Here are some of them:
- Detection Gap: Currently, the burden of detecting malicious activities rests on the organisation or individual. This is a problem because most civil society organisations in the Global South lack the internal technical capacity to identify advanced threats or stealth attacks by well-resourced state actors. As a result, an at-risk organisation will only contact a help desk when it visibly detects an issue – leaving a critical gap in situations where there are more subtle or complex threats.
- Reactive Response: This reactive approach primarily addresses attacks only after they have occurred and succeeded, making incident response for CSOs more about damage control than prevention. As a result, digital resilience for CSOs in the Global South is limited to focusing on post-attack recovery rather than proactive protection.
- Time-consuming: This approach can take anywhere from 2 to 10+ days to resolve a complex threat or attack, which provides ample time for any threat actor to inflict significant damage, exfiltrate sensitive data and disrupt the operations of an organisation.
- Limited Threat Data: For effective threat management, accurate and comprehensive threat data is critical, yet, many help desks rely on incident reports from CSOs, most of whom cannot detect threats beyond obvious phishing or social media attacks. This, consequently, limits the quality and quantity of threat data help desks are able to collect, process and share with their community.
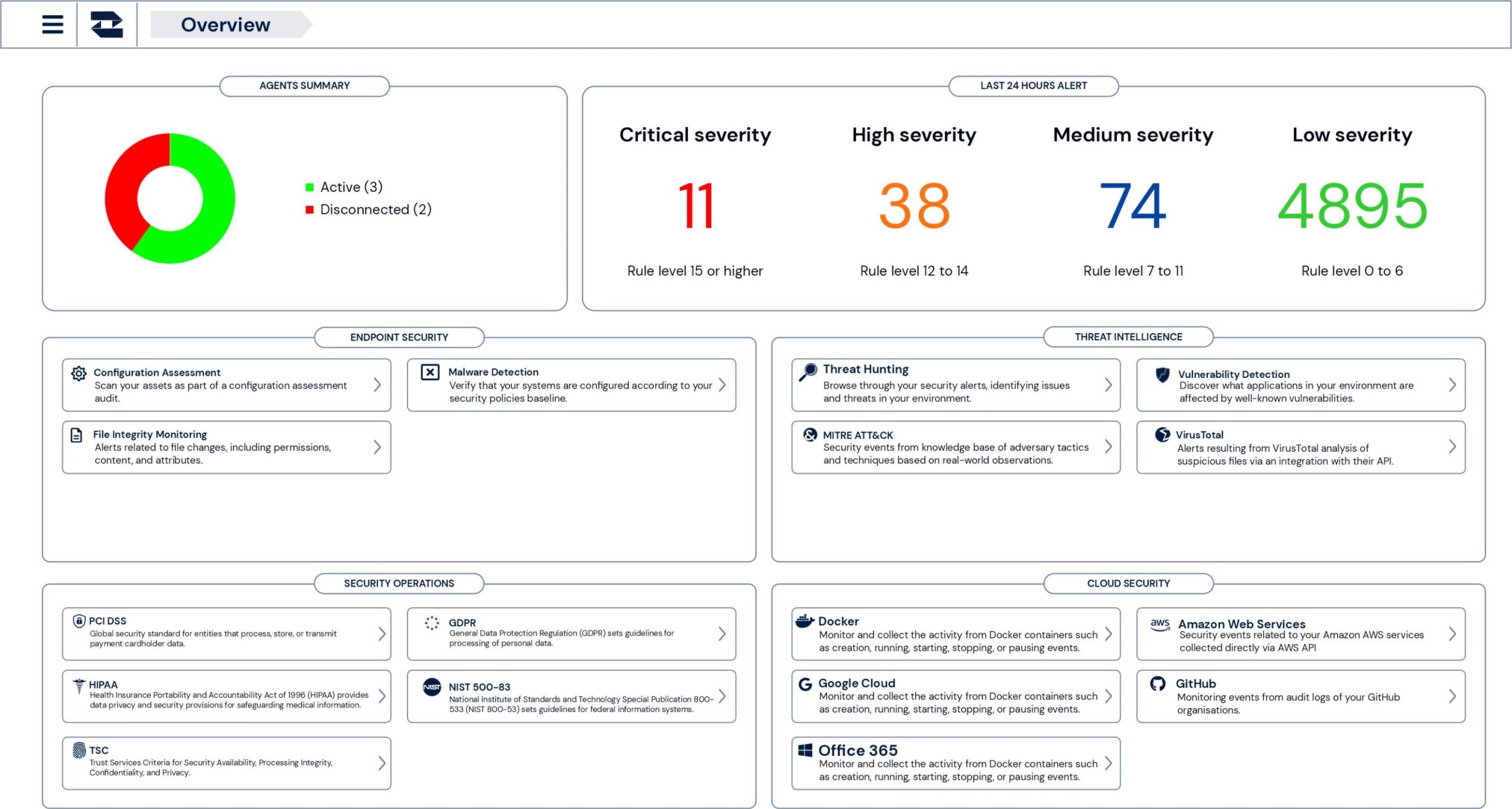
…Enter Zeroth Cloud – An automated, AI-enabled, zero-trust threat management solution.
Zeroth Cloud solves all the above issues, and more. What we have put together is a solid architecture of open-source technologies leveraging artificial intelligence to automate the entire lifecycle of threat management including prevention, detection and response with minimal human interaction. The Zeroth Cloud agents (or z_agents) constantly monitor the environments where they are deployed (such as laptops, mobile, endpoints, containers, websites, cloud infrastructure like Office 365, and so on) for threats, flaws, misconfigurations and deviations from set policies and rules. When a threat is detected, the agents immediately isolate the impacted environment, execute a remedy action and log the details of the threat/incident on an operator dashboard for further review and action.
By deploying Zeroth Cloud for organisations, we can now achieve;
- Proactive Threat Management: Old, new, and unknown threats are prevented through proactive detection and remediation. Detection no longer depends on individuals within an organisation, but on automated, AI-enabled systems which monitor key infrastructure and protect them round the clock.
- Fast and Automated Response: Zeroth Cloud isolates and neutralises threats continuously and autonomously while providing detailed threat reports for further investigation. A detection, response, and reporting cycle can be completed in under an hour, markedly reducing response time and risk exposure for organisations.
- Simplified Expertise: Integrations with multiple threat and malware databases (like Mitre ATT&CK, MISP, VirusTotal, etc) enables even average help desk analysts to handle intermediate-level threat and forensic investigations with greater ease.
- Shared Threat Intelligence: Rich, contextualised threat data is generated which can be shared with communities, help desks, and platforms like Leafcutter for proactive planning, support and intervention.
Our Vision
We envision a world where access to threat management is democratised, and every organisation- big or small- can proactively manage the prevention, detection and response to cyber threats with little or no technical knowledge.
Our vision for Zeroth Cloud is captured by five key terms:
- Access: A solution that is accessible and affordable to organisations at risk
- Impact: A solution that is effective in addressing the challenges of threat prevention, detection and response
- Sustainability: A solution that is continuously accessible and usable, and is not tied to the lifecycle of a grant or project.
- Scalability: A solution that is not limited by platform, technology, language or in the number of users or deployments possible
- Democratisation: A solution that can be set up and managed by a non-technical end user with zero support or guidance
For the next 4 years, we will be solving for each of these across three key phases:
Phase 1: Launch X 100
From January 2025, we will launch the first phase of Zeroth Cloud deployments, prioritising organisations most at-risk, with a particular focus on African organisations.
Zeroth Cloud will start at $4,000 per annum for medium-sized organisations.
You can join the waitlist here or contact us at info@rtafrica.org to get a free trial from January 2025.
Our goal in this phase is to deploy for 100 organisations who will get protection for their assets and infrastructure all year round.
We are currently working to make this free for organisations under active attacks but cannot afford it.
Phase 2: Scale X 1,000
In 2026, we will enter the second phase and begin deployment of instances for help desks and operators who manage security for at-risk organisations. With their own dedicated instance of Zeroth Cloud, help desks can more proactively provide threat management support to organisations at-risk, and at reduced cost. Resilience Technologies will provide technical and administration support to these help desks as they run their own instances. Our goal here is 15 – 20 managed instances for help desks supporting 50+ organisations each.
Zeroth Cloud becomes significantly cheaper at this stage with some of the current engineering problems solved for. We estimate that a medium-sized organisation can pay anywhere from USD 700 – 1300 to cover server/storage costs and have Zeroth Cloud operational for them, protecting all assets and infrastructure with timely, dedicated reporting and support for an entire year.
Phase 3: Capsule
In the final phase- and our long-term goal for Zeroth Cloud; the democratisation of threat management expertise- we will build the Zeroth Capsule; a robust application solution that combines the three key threat management pillars, namely; prevention, detection, and response, on one platform. Users can simply download the application on different organisational assets and infrastructure like laptops, network devices, cloud systems, etc, and manage the entire experience from their mobile phones.
We are excited about this journey and eagerly look forward to our first few deployments.
Again, you can join the waitlist here.
